When we communicate and share sensitive information online, it’s crucial to ensure that it’s secure and protected. Cryptography is a technique that helps achieve this by converting messages into codes. It plays an active role in network security, confirming that only the intended receiver can access and understand the information, thus preventing unauthorized access.
Let’s take a small step together towards understanding cryptography, its various techniques, and its importance in maintaining network security. We’ll discuss how cryptography is used to ensure safety and security in online communication and why it’s essential to do so.
To make it easier to understand, we’ll avoid using as many complicated words, jargon, or legal language as possible. Instead, we’ll use everyday language and keep sentences short.
Understanding Cryptography
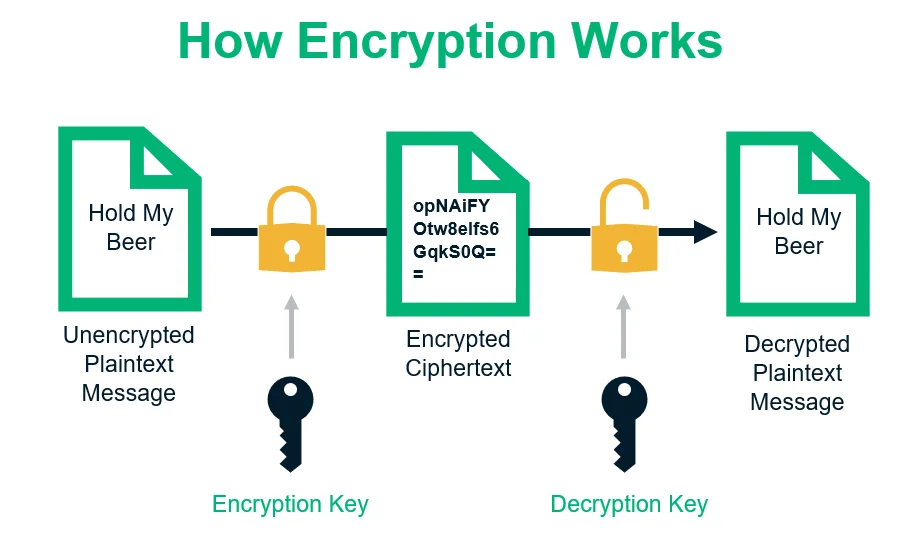
Cryptography keeps information secure by using math and algorithms to turn plain text into code. Encryption turns a message into an unreadable form, so only authorized people can read it. Decryption changes the code back to the original message. Cryptography has several features that keep information safe:
Confidentiality: Cryptography ensures that information can only be accessed by its intended recipient. The use of encryption algorithms and keys makes it extremely difficult for unauthorized individuals to decode the ciphertext.
Integrity: Cryptography protects the integrity of information by detecting any unauthorized modifications or alterations. It ensures that data remains unchanged during storage and transmission, allowing recipients to verify its authenticity.
Non-repudiation: Cryptography establishes accountability by preventing the sender of a message from denying their intention to send it. Digital signatures, a cryptographic technique, ensure that the sender cannot later claim that the message was fraudulent or deny their involvement.
Authentication: Cryptography enables the confirmation of the identities of both the sender and receiver of information. By using cryptographic keys, individuals can establish and verify the authenticity of messages and validate the source of the information.
Types of Cryptography
Cryptography can be classified into three main types, each serving different purposes in securing information:
Hash Functions
Hash functions play a role in securing passwords and ensuring data integrity. They generate a fixed-length hash value based on the input data, making it nearly impossible to retrieve the original plaintext from the hash value. Operating systems commonly use hash functions to encrypt passwords, ensuring that even if the password database is compromised, the passwords remain unreadable.
Symmetric Key Cryptography
Symmetric key cryptography, i.e., secret key cryptography, is a way to encode and decode data using a shared secret key. The sender and receiver both use this key to read and write messages. It’s a straightforward and efficient system, but the key must be exchanged securely. Some popular symmetric key algorithms are the AES (i.e., Advanced Encryption Standard) and the DES (i.e., Data Encryption Standard).
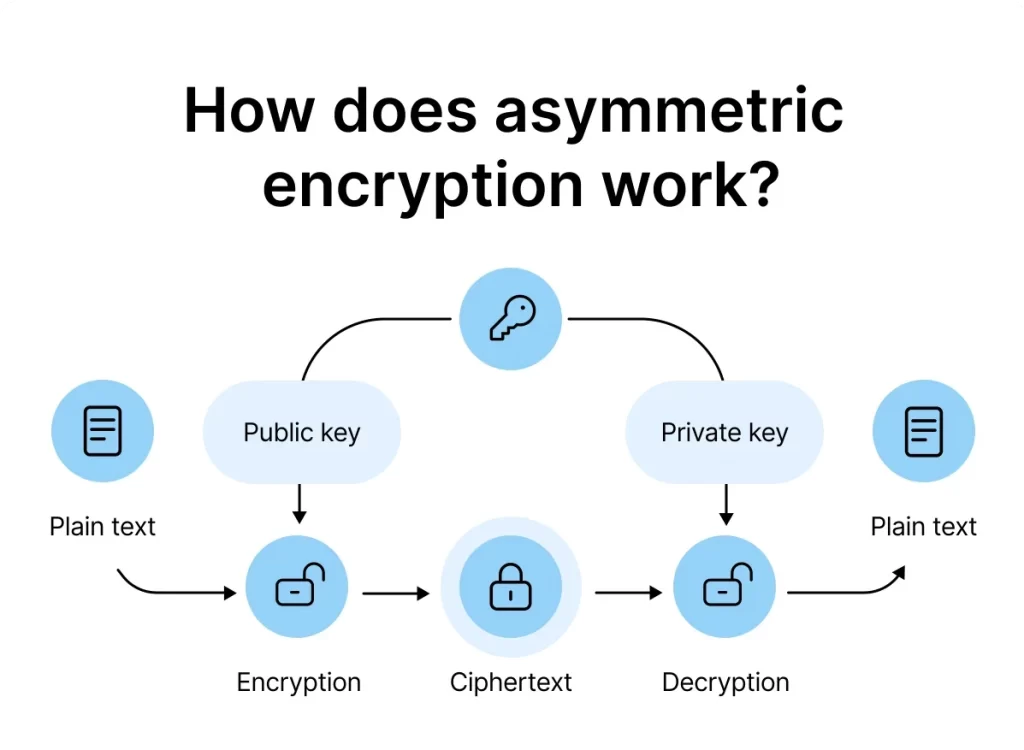
Asymmetric Key Cryptography
Asymmetric key cryptography, i.e., public key cryptography, employs a pair of keys for encryption and decryption. The recipient’s public key is used for encryption, while the recipient’s private key is used for decryption. Unlike symmetric key cryptography, the public key can be freely distributed, allowing anyone to send encrypted messages to the intended recipient. The most widely used asymmetric key algorithm is the RSA algorithm.
Applications of Cryptography
Cryptography has a wide range of use cases in various fields, ensuring the security and integrity of sensitive information. Let’s explore some of the key areas where cryptography is extensively used:
- Computer Passwords
Cryptography is a necessary part of securing computer passwords. When someone logs in, their password is turned into a hash value and checked against the stored hash. Encrypting passwords is important because it prevents hackers from understanding passwords even if they gain access to the password database.
- Secure Web Browsing
Cryptography is a way to keep browsing safe; it protects users from spying and attacks. When web servers and clients communicate, they need to make sure that nobody else can see or access their information. To do this, they use protocols like Secure Socket Layer (SSL) and Transport Layer Security (TLS), which use public key cryptography to keep the data secure. This means that nobody can read the data that is transmitted between the web servers and clients.
- Blockchain
Blockchain technology uses cryptography to protect user privacy and transaction information, and to ensure consistent data.
- Electronic Signatures
Electronic signatures, created using cryptography, serve as the digital equivalent of handwritten signatures. They provide a means to sign and validate documents securely. Digital signatures are created based on public key cryptography and can be verified using the recipient’s public key.
- Authentication
Cryptography is essential for authentication in various scenarios, such as accessing bank accounts, logging into computers, or using secure networks. Authentication protocols employ cryptographic methods to confirm a user’s identity and verify their access rights to specific resources.
- Cryptocurrencies
Cryptocurrencies like Bitcoin and Ethereum heavily rely on cryptography to safeguard transactions, prevent fraud, and maintain the integrity of their networks. Complex algorithms and cryptographic keys provide robust security measures for these digital currencies.
- End-to-End Encryption
End-to-end encryption provides the privacy and security of two-way communications, such as video calls, instant messages, and emails. By encrypting the message, only the intended recipients can decipher its content. Popular communication apps like WhatsApp and Signal employ end-to-end encryption to protect user communications.
Advantages of Cryptography
Cryptography offers several advantages in the realm of network security:
Access Control: Cryptography can control who has access to a company’s database. Only authorized workers with the correct decryption key can get in. This keeps protected information safe.
Secure Communication: Cryptography plays a crucial role in secure online communication, providing mechanisms for the safe transmission of sensitive information over the Internet.
Protection against Attacks: Cryptography helps protect against attacks like replay and man-in-the-middle attacks. It offers techniques to detect and prevent them. By using cryptography, you can make sure that your data is kept safe.
Compliance with Legal Requirements: Cryptography assists organizations in meeting legal requirements, including data protection and privacy laws. By implementing cryptographic measures, companies can ensure compliance with regulations.

Frequently Asked Questions (FAQ)
Is cryptography only used for securing digital?
No, cryptography is also used to secure physical information. For example, cryptography techniques are employed in bank cards to protect transactions and ensure the privacy of sensitive financial data.
Is it possible for a cryptographic algorithm to be completely unbreakable?
While cryptographic algorithms are designed to be highly secure, there is always a possibility of vulnerabilities being discovered or advances in computing power, making specific algorithms susceptible to attacks. However, modern cryptographic algorithms are rigorously tested and constantly updated to mitigate such risks.
Can someone with access to the encrypted message decrypt it without the decryption key?
When we use symmetric key cryptography, it’s almost impossible to decrypt a message without the decryption key. On the other hand, with asymmetric key cryptography, any person can use the public key to encrypt the message, but only the person who has the private key can decrypt it.
Cryptography is a grand part of network security that helps keep information confidential, authentic, and secure. It is done through various techniques that we’ve discussed, such as symmetric key cryptography, asymmetric key cryptography, and hash functions. These techniques are used to protect sensitive data and communications from unauthorized access and tampering. Cryptography remains an essential tool to safeguard information in the digital age and will continue to evolve as technology advances.





